Abstract
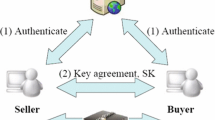
Three-party password-based authenticated key exchange (3PAKE) protocols allow two clients to establish a secure session key through a server over an insecure channel. Recently, the 3PAKE protocols have been developed based on Chebyshev chaotic maps, in which the clients utilize smart cards to login into the server and employ server’s public key to ensure the identity of the server or symmetric cryptosystems to encrypt the messages. However, this paper describes an efficient chaos-based 3PAKE protocol without smart cards, which requires neither server’s public key nor symmetric cryptosystems. The security of the proposed 3PAKE protocol is proved in the random oracle model using the chaos-based decisional Diffie–Hellman assumption. In comparison with the existing chaos-based 3PAKE protocols, our protocol individually provides better performance in terms of communication, computation, and security aspects, and is supported by the formal proof in the random oracle model.




Similar content being viewed by others
References
Guo, C., Chang, C.C., Sun, C.Y.: Chaotic maps-based mutual authentication and key agreement using smart cards for wireless communications. J. Inf. Hiding Multimedia Signal Process. 4(2), 99–109 (2013)
Farash, M.S., Bayat, M., Attari, M.A.: Vulnerability of two multiple-key agreement protocols. Comput. Electr. Eng. 37(2), 199–204 (2011)
Farash, M.S., Attari, M.A., Bayat, M.: A certificate less multiple-key agreement protocol without one-way hash functions based on bilinear pairings. IACSIT Int. J. Eng. Technol. 4(3), 321–325 (2012)
Farash, M.S., Attari, M.A., Atani, R.E., Jami, M.: A new efficient authenticated multiple-key exchange protocol from bilinear pairings. Comput. Electr. Eng. 39(2), 530–541 (2013)
Farash, M.S., Attari, M.A.: Provably secure and efficient identity-based key agreement protocol for independent PKGs using ECC. ISC Int. J. Inf. Secur. 5(1), 18–43 (2013)
Farash, M.S., Attari, M.A.: A pairing-free ID-based key agreement protocol with different PKGs. Int. J. Netw. Secur. 16(2), 143–148 (2014)
Haiyan, S., Qiaoyan, W., Hua, Z., Zhengping, J.: A strongly secure pairing-free certificate less authenticated key agreement protocol for low-power devices. Inf. Technol. Control. 42(2), 105–112 (2013)
Jiang, Q., Ma, J., Li, G., Ma, Z.: An improved password-based remote user authentication protocol without smart cards. Inf. Technol. Control. 42(2), 150–158 (2013)
Tang, H.B., Liu, X.S., Jiang, L.: A robust and efficient timestamp-based remote user authentication scheme with smart card lost attack resistance. Int. J. Netw. Secur. 15(6), 360–368 (2013)
Kumari, S., Gupta, M.K., Khan, M.K., Li, X.: An improved timestamp-based password authentication scheme: comments, cryptanalysis, and improvement. Secur. Commun. Netw. (2013). doi:10.1002/sec.906
Farash, M.S., Attari, M.A.: An enhanced authenticated key agreement for session initiation protocol. Inf. Technol. Control. 42(4), 333–342 (2013)
Bayat, M., Sabzinejad, M., Movahed, A.: A Novel Secure Bilinear Pairing Based Remote User Authentication Scheme with Smart Card. In: IEEE/IFIP 8th International Conference on Embedded and Ubiquitous Computing (EUC), pp. 578–582 (2010)
Xie, Q.: Improvement of a security enhanced one-time two-factor authentication and key agreement scheme. Sci. Iran. 19(6), 1856–1860 (2012)
Xie, Q., Dong, N., Tan, X., Wong, D.S., Wang, G.: Improvement of a three-party password-based key exchange protocol with formal verification. Inf. Technol. Control. 42(3), 231–237 (2013)
Lee, T.F., Chang, I.P., Wang, C.C.: Efficient three-party encrypted key exchange using trapdoor functions. Secur. Commun. Netw. 6(11), 1353–1358 (2013)
Xiong, H., Zhong, C., Fagen, L.: New identity-based three-party authenticated key agreement protocol with provable security. J. Netw. Comput. Appl. 36(2), 927–932 (2013)
Xiong, H., Chen, Y., Guan, Z., Chen, Z.: Finding and fixing vulnerabilities in several three-party password authenticated key exchange protocols without server public keys. Inf. Sci. 235(1), 329–340 (2013)
He, D., Zhang, Y., Chen, J.: Cryptanalysis of a three-party password-based authenticated key exchange protocol. Int. J. Netw. Secur. 16(4), 281–284 (2014)
Wu, S., Chen, K., Zhu, Y.: Enhancements of a three-party password-based authenticated key exchange protocol. Int. Arab J. Inf. Technol. 10(3), 215–221 (2013)
Liu, T., Pu, Q., Zhao, Y., Wu, S.: ECC-based password-authenticated key exchange in the three-party setting. Arab J. Sci. Eng. 38(8), 2069–2077 (2013)
Pu, Q., Wang, J., Wu, S., Fu, J.: Secure verifier-based three-party password-authenticated key exchange. Peer Peer Netw. Appl. 6(1), 15–25 (2013)
Tso, R.: Security analysis and improvements of a communication-efficient three-party password authenticated key exchange protocol. J. Supercomput. 66(2), 863–874 (2013)
Wu, S., Pu, Q., Wang, S., He, D.: Cryptanalysis of a communication-efficient three-party password authenticated key exchange protocol. Inf. Sci. 215(1), 83–96 (2012)
Li, H., Hu, L., Chu, J., Chi, L., Li, H.: An efficient three-party authentication key exchange protocol for wireless sensor networks. Sens. Lett. 11(5), 990–996 (2013)
He, D., Chen, Y., Chen, J.: An ID-based three-party authenticated key exchange protocol using elliptic curve cryptography for mobile-commerce environments. Arab J. Sci. Eng. 38(8), 2055–2061 (2013)
Xing-Yuan, W., Da-Peng, L.: A secure key agreement protocol based on chaotic maps. Chin. Phys. B. 22(11), 110503 (2013)
Tan, Z.: A chaotic maps-based authenticated key agreement protocol with strong anonymity. Nonlinear Dyn. 72(1–2), 311–320 (2013)
Chen, T.H., Wang, B.J., Tu, T.Y., Wang, C.H.: A security enhanced key agreement protocol based on chaotic maps. Secur. Commun. Netw. 6(1), 108–114 (2013)
Lee, C.C., Hsu, C.W.: A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn. 71(1–2), 201–211 (2013)
He, D., Chen, Y., Chen, J.: Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dyn. 69(3), 1149–1157 (2012)
Lee, C.C., Chen, C.L., Wu, C.Y., Huang, S.Y.: An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dyn. 69(1–2), 79–87 (2012)
Yoon, E.J.: Efficiency and security problems of anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7), 2735–2740 (2012)
Xue, K.P., Hong, P.L.: Security improvement on an anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7), 2969–2977 (2012)
Guo, C., Chang, C.C.: Chaotic maps-based password-authenticated key agreement using smart cards. Commun. Nonlinear Sci. Numer. Simul. 18(6), 1433–1440 (2013)
Gong, P., Li, P., Shi, W.: A secure chaotic maps-based key agreement protocol without using smart cards. Nonlinear Dyn. 70(4), 2401–2406 (2012)
Lee, C.C.: A simple key agreement scheme based on chaotic maps for VSAT satellite communications. Int. J. Satell. Commun. N 31(4), 177–186 (2013)
Lee, C.C., Hsu, C.W., Lai, Y.M., Vasilakos, A.: An enhanced mobile-healthcare emergency system based on extended chaotic maps. J. Med. Syst. 37(5), 9973 (2013)
Lai, H., Xiao, J., Li, L., Yang, Y.: Applying semigroup property of enhanced Chebyshev polynomials to anonymous authentication protocol. Math. Prob. Eng. (2012). doi:10.1155/2012/454823
Zhao, F., Gong, P., Li, S., Li, M., Li, P.: Cryptanalysis and improvement of a three-party key agreement protocol using enhanced Chebyshev polynomials. Nonlinear Dyn. 74(1–2), 419–427 (2013)
Lee, C., Li, C., Hsu, C.: A three-party password-based authenticated key exchange protocol with user anonymity using extended chaotic maps. Nonlinear Dyn. 73(1–2), 125–132 (2013)
Xie, Q., Zhao, J., Yu, X.: Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dyn. 74(4), 1021–1027 (2013)
Li, Z., Cui, Y., Jin, Y., Xu, H.: Parameter selection in public key cryptosystem based on Chebyshev polynomials over finite field. J. Commun. 6(5), 400–408 (2011)
Rosenberg, J., Schulzrinne, H., Camarillo, G., Johnston, A., Peterson, J., Sparks, R., Handley, M., Schooler, E.: SIP: session initiation protocol. RFC 3261, June 2002.
Abdalla, M., Pointcheval, D.: Interactive Diffie–Hellman assumptions with applications to password-based authentication. In: Proceedings of FC’05, LNCS 3570, 2005, p. 341356.
Xue, K., Hong, P.: Security improvement on an anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 17(7), 2969–2977 (2012)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Farash, M.S., Attari, M.A. An efficient and provably secure three-party password-based authenticated key exchange protocol based on Chebyshev chaotic maps. Nonlinear Dyn 77, 399–411 (2014). https://doi.org/10.1007/s11071-014-1304-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-014-1304-6